
The Thong I Should Be Wearing [UPDATE] by Snively '11
Sexy sexy undies.
Wait. . . what? Thongs? MIT? Together?
Here’s the story. Well, actually, here’s the backstory, then the story.
Back in July 2006 there was an issue with the Doonesbury comic strip. The main character’s daughter in the comic strip, Alex, had to decide which college to go to. She was accepted to several tech schools and the comic strip writer decided that he’d leave it up to a vote to decide where she went. He put up an online poll and, well —

I read this before I came to MIT and thought it was one of the funniest things ever. I lol’d and lol’d, and then Melis wrote a wrap up entry that showed the end result of MIT’s poll-bombing.

Fast forward a couple of years. Here’s what happened this time.
An e-mail got sent to several sororities, telling them about a new contest that Victoria Secret was having for their collegiate Pink! line. They had a list of 31 colleges and you could vote for yours. Whichever college had the most votes after an unspecified amount of time would be declared the winner and would have their own line of Pink! clothing.
BUT! This wasn’t just an e-mail. This was a special e-mail. This was an e-mail with an HTML file attached to it. An html file that, when opened in a browser, would register up to four votes per second for MIT. I smell another poll-bombing!
That e-mail was subsequently e-mailed to the East Campus dorm list and that’s when the fun began. The script was opened up on multiple servers, dozens of computers, hundreds of windows, and thousands of tabs, each voting four times a second. MIT, which used to be at 300,000 votes was soon to be catapulted to the upper echelon of schools in the contest. Drexel already had about 5,000,000 votes, meaning they had obviously run a script as well, but nowhere nearly as vigorous as us.
Then all hell broke loose. The hack was sent to all of the class lists, meaning every single student at MIT had the script in their inbox. The e-mail thread that followed was hilarious! Here are some excerpts.
Looks like Drexel already had the idea (nobody really likes them that much, right?). No worries though, at this rate we’ll be #1 in about 6 hours. —————————————————————
wow, looks like we killed the MIT node…akamai is shuffling the requests around now…that means new servers to overload!
—————————————————————
It’s not just the MIT node… I’m in Ohio and I’m getting the same major delays to the site that you guys are.Also, I just did a measure of your voting rate over 5 minutes:
Start: 1,288,966
Finish: 1,344,741
=
11,155 votes per minute.Drexler is currently averaging only 400.8 votes per minute.
Rock on, MIT.
—————————————————————
That means we have to overtake Drexler before the PINK server melts.
—————————————————————
I think we melted it…I just tried to check the rankings and got and got an
error message that says “Sorry: We’re working fast to make improvements to this
area. Check back soon to nominate your school!”
—————————————————————
(DRAMATIZATION)root@pink-server # tail -50 /var/www/logs/http/access.log | cut -d” ” -f 1,4,6
18.238.1.200 [21/Oct/2008:20:46:43 “POST
18.248.0.106 [21/Oct/2008:20:46:44 “POST
18.238.2.127 [21/Oct/2008:20:46:44 “POST
18.238.6.84 [21/Oct/2008:20:46:45 “POST
18.238.2.127 [21/Oct/2008:20:46:47 “POST
18.248.3.109 [21/Oct/2008:20:46:49 “POST
18.240.2.220 [21/Oct/2008:20:47:01 “POST
18.238.2.127 [21/Oct/2008:20:47:01 “POST
18.244.1.147 [21/Oct/2008:20:47:03 “POST
18.238.1.200 [21/Oct/2008:20:47:04 “POST*scratches head* Gee.. I wonder where all these 18.*.*.* IP’s are coming from?
(/DRAMATIZATION)
—————————————————————
For a short amount of time the website was back up with a “fix” that prevented script voting. Essentially, they just added a cookie that wrote vote=”true” if you voted. Everybody turned off cookies and went back to it, crashing the server again.
Crashed. We’re talking gone, nobody (not even my family in Oregon) could access it. Then, magically, a day or two later, it reappeared. The attack was back on! But. . . wait . . . votes for MIT weren’t being counted! It didn’t matter where the votes were coming from, Victoria Secret had completely locked out the top several schools from voting, including MIT.
The e-mail thread blazed on.
I just sent an email to the vSPINK people using their “contact us” form. I complained that they really need to fix their broken app so that the other 3 million students here at MIT can voice their school pride.
We’ll see how it goes.
The effort split at this point. One group of people created a mailing list devoted to reverse engineering the code on Victoria Secret’s website so that they could unlock MIT’s votes. Another group set to running the scripts on some of their favorite other schools. Suddenly, schools you’d never expect to have their own Victoria Secret clothing lines were creeping up the leaderboard. At this point, the website looked like this:
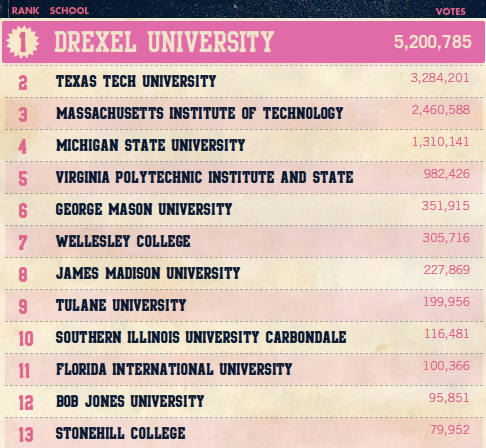
We had gone from 300,000 to 2.4 million in less than a day. Rock. Also, note the appearance of George Mason University, Wellesley College, and Bob Jones University. None of them had actually been on the leaderboard earlier. This is right at the onset of MIT’s attempt to level the playing field, running scripts for the colleges we thought needed some extra votes. What did the leaderboard look like today?

HAHAHAHAHA!!! LOOK AT NUMBER SEVEN!!! HAHAHAHAHAHA!!!
Also, look at how many points George Mason University earned! 2.4 Million! I’ve just gotta say, good show MIT, good show.
[Ok, quick note. I’ve received a number of e-mails from students at GMU and apparently they ran all their own scripts. Obviously, I had no way of knowing this, but kudos to y’all. MIT did help a bit, but obviously not nearly as much as I thought. We’d still like to take credit for Zion Bible College, assuming nobody there wrote any scripts]
Now. . . here’s the amazing part. I can’t access VSPink.com. Nobody at MIT can. Any IP address that starts with 18 (MIT’s personal IP address) is instantly blocked. Sara ’12, who’s at home this weekend, sent me some screenshots though, and I’ve noticed some renovations to the Victoria Secret website. First change, a new little block of text above the voting box.
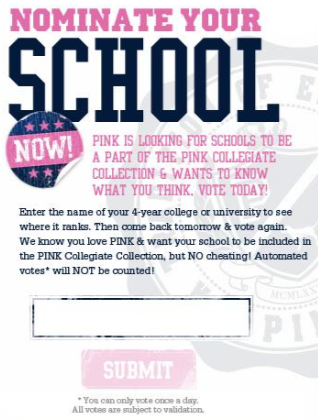
NO cheating. Ha. Sure. So, it’s not really cheating unless it’s against the rules, and there were never any rules.
The next addition was a little pink star above the top list of schools.

On to us? LOL, busted. But, hey, it looks like we won a free visit from the Victoria Secret Pink! crew, rock on!
Finally, their last lovely addition, was a captcha system.
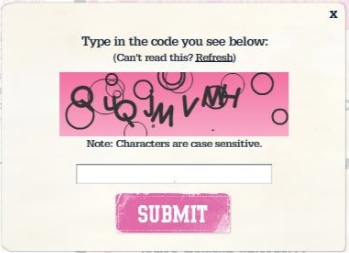
We’re kinda stuck now. Our scripts don’t actually break captchas. But, it was an epic battle between the MIT students and the Victoria Secret SysAdmins, and hopefully there are no hard feelings. We had a great time and based on Victoria Secret’s new little warnings on their website, they had a good time protecting their site from us.
No, we didn’t win, but that’s ok. Sometimes it’s not about winning, it’s about the fight and the competition, something we definitely enjoyed.
Oh, by the way, if you aren’t at MIT, you can still vote for us, so head over to their website and vote for us! We can do it!
Whoopie!
First.
Very colorful and nice post though. Keep it up Snively.
this is hilarious lol
Great post.
I actually voted!
Do you know how Alex is doing?
I just voted for MIT, but we slipped one place in just a second Snively, we are currently ranked #4 instead os #3 a second before my vote.
It took them until MIT crashed the servers to start using captchas?
Very nice post though Snively
oops! it should be “of” in my last response last line above.
I think there is some weird hacking going on at George Mason University, they are having abot 800 (approx) votes a second i guess.
Nice post Snively. Showing what we students (especially freshmen) do to avoid psetting and studying for exams… Lol.
And lol at the new additions they made on the site.
Dear God, that is so epic.
Hilarious. I voted!
Ding it!
Forgot the “t” in the ‘want’ above.
ONLY two hours and fifty six minutes for EARLY ACTION deadline.
George Mason University is catching up? I’ll try sending some messages to a student there to see what is going on there.
Rofl, the bible school with a pink clothing line.
I’m suprised CalTech didn’t start at it, too.
Ugh, had to make last minute changes to Part 2.
Almost done…
Rofl.. so after consecutive server crashes they
1) added a cookie
2) banned votes for MIT
3) banned 18.*.*.* (did anyone think to use a proxy)?
4) finally found out about captcha
Very good ^^
There are scripts out their to break the captcha!
I’m not computer genius, but aren’t there also methods or programs out there that mess or skew with your IP address in some fashion to make you effectively anonymous.
I don’t remember exactly what it was, I just read about it in an article about people who used it in China to look at sensitive sites w/o getting arrested.
go Zion!
Why did people decide to vote for GMU again?
I say you guys go crash the BPL
I voted for MIT! Wahoo!
I think it’s great so many MIT students worked together to crack their system!
CalTech??? Have they heard of Victoria’s Secret??
Great post Snively!
Oh man was that ever good fun. We had the entire athena cluster running the script in 4 tabs each. Then when they gave out their cookie name we ran a bash script that was even faster, it bypassed the entire voting window and just pinged the crap out of the voting servers. I take it as a victory that we made them change the rules and put up banners about us. Infamy> Fame
Awesome! (:
-votes!-
shucks…and I was gonna get myself some PINK wear if MIT won…and seriously..they should just chill out and just make the MIT PINK wear for our effort..like Doonesbury
This is the type of stuff that makes me wonder why a nerd would want to go anywhere else for college. I feel sorry for the people who are accepted here but deny the offer.
Our company offers state of the art technology on CAPTCHA solving by using our patented Sweatshop 2.0 humanbots.
Our service provide around 1 CAPTCHA per second for one single processing humanbot. The entire human farm can produce a whopping 10^6 CAPTCHA per second.
Please contact us if you are interested.
THIS IS SERIOUSLY FUNNY!!!
You really know how to title a post :D
Good post~
So far I have voted twice. Snively — I’ll see to it that you get your thong.
I burst out laughing. MIT has my vote.
I’m likin’ the httpd server log dramatization…
come on guys MIT is averaging about ONE vote every 3 minutes. We wan our dream school on the top.
proxy?
just to clear a few things up
george mason had their own scripts running (just like every other school) don’t try to think that you helped us get up there. a lot of dedicated students ran the script daily and i dont think you woulda ran the script in order for us to beat you guys. that’s just dumb and we had our own IT kids helping us get out the votes.
@gmu student
Obviously there was no way of me knowing whether you guys were running scripts or not. Yes, we were running scripts for you guys, along with running scripts for John Brown and Zion Bible college. I guess your scripts and our scripts just boosted you guys even more.
I was the texas tech kid who started the auto voting. Not bragging of course but anyway. The other schools that were auto voting reversed engineered the flash player. I coded my program in .net and ran it on 1 computer. The Drexel kids were running 6 computers on 2 T1 connections and the George Mason kid was running on 2 computers. So I guess MIT isn’t as cool as I thought it was with it’s army of dorm computers. The captcha that they added actually doesn’t do anything as far as stopping the auto voting from my perspective. If there’s any MIT kids who want to talk shop here’s my email [email protected].
Actually, the kid voting for GMU was not MIT. A friend of mine wrote a script that surpassed the entire website and simply sent spoofed packets to the vspink server allowing him to vote hundreds of times per second.
He single-handedly brought GMU up to second place.
http://media.www.thetriangle.org/media/storage/paper689/news/2008/11/14/News/Students.Fool.pink.Poll-3544538.shtml
One small point: Drexel’s was executed solely by two students, hence their “less vigorous” attempt.
@travis above:
To use the actual vspink website one _has_ to bypass the captcha. Obviously to overcome this, one could send spoofed packets directly to the vote counting server as it is not configured particularly smartly. (There is no reverse proxy gateway verifying that connections are actually from where they claim to be…). However, exploiting the server this way is a clear ddos attempt. Previously, we were not doing anything that was expressly forbidden by the contest rules. If we spoofed packets, we would be. Also, since MIT is a class A network, all our IPs start with 18., so writing a script on the server to ignore any votes from ips that start with 18. would not be hard at all. If we were to hunt the internet for proxies or use something like a tor chain for this purpose, it would just be weak and IMO taking it too far along the ‘malafide intent’ track rather than a ‘hmm, a new programming challenge’ track. Hence we decided to stop.
Also, about your remark saying people reverse engineered flash, you used .net etc. That’s all fine, but not really necessary.
curl ‘www.vspink.com/services/university_count.jsp?universityName=Massachusetts Institute of Technology’2>/dev/null;
with lots of fork()s and a for loop were all that was necessary initially. Later, we had to figure out that tokenString = md5( ‘51945594359056937919959842284083772614’ + keyString ) and add that.
— Resident of EAsT camPUS dorm, MIT